Blog Date: 10/23/2017
Author: Ray Coulombe
Real Life SQLI Examples
As Time magazine reported in their July 20, 2017 article, “Inside the Secret Plan to Stop Vladimir Putin’s U.S. Election Plot,” hackers targeted a number of state voter registration and election sites, including the state of Illinois. In one Illinois jurisdiction, as the article states, “instead of entering his personal information in one of the fields for names and addresses, the hacker uploaded a string of malicious prewritten code, executing a classic hack known as SQL Injection (SQLI). With that, the hacker opened a back door to all 15 million files on past and current voters in the state since 2006. And for nearly three weeks, no one knew he was there.”
Companies small and large aren’t immune. In fact, many smaller firms and individuals use WordPress to construct their web sites, yet it’s an environment which is known historically to be vulnerable. Wordfence reports that 18 percent of the nearly 1,600 WordPress vulnerabilities enumerated over 14 months were SQL Injection based.
A Veracode analysis has determined that our Federal Government has the highest prevalence of easily exploitable vulnerabilities like SQL Injections and cross-site scripting. Want to see more examples? Visit http://codecurmudgeon.com/wp/sql-injection-hall-of-shame.
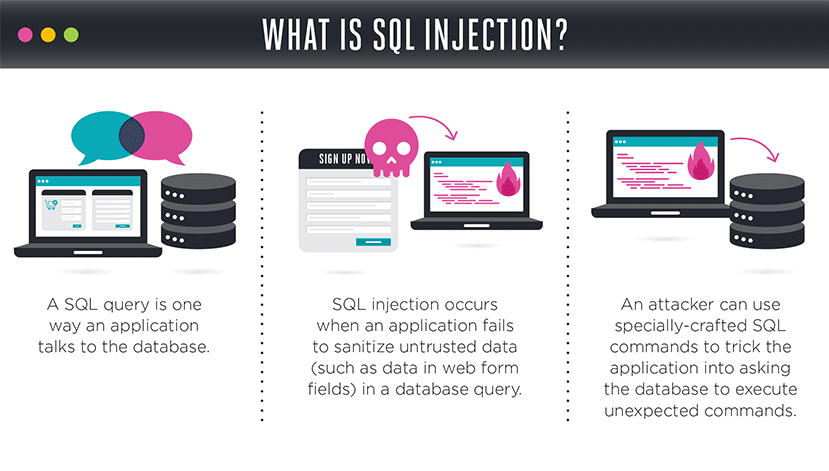
SQL stands for Structured Query Language which provides an architecture, structure, and syntax for constructing and interacting with relational databases. Among its database functions, SQL can execute queries, retrieve data, and insert, delete, and update records.
Objectives for SQLI attacks differ, but include:
- Theft of financial information
- Theft of personal or personnel information
- Theft of competitive information
- Strategic, or state-sponsored
- General mischief or damage
- Privilege escalation and control
How it Works
Database-driven web applications typically contain server-side script written in a programming language that extracts information from a back-end database in a user-driven process. A client-side interface passes information to the web server that calls an API from the application server (e.g., a database server). The database application will reach into the database to fulfill the request. An example of a statement (drawn from my own website) passed to the web server is found here, which is requesting product information from a company whose ID in the database is 496. The “?” is a separator preceding the query string. Manipulating the query string is a means to work your way into the database or to tickle enough information out to further refine the attack strategy. A successful SQLI attack requires the attacker to construct a syntactically correct SQL Query to present to the logic tier.
At this point, you might ask what this has to do with our world pf physical and electronic security. For starters, most enterprise access control systems use relational databases to store everything from users to privilege levels to credentials and more. SQLI is a potential vulnerability along with an attack known as cross-site scripting (XSS). Further, LDAP (Lightweight Directory Access Protocol) is being increasingly used for enterprise-wide access and may also be subject to these injection attacks.
How to Protect Your Applications
Manufacturers should take a number measures to protect their applications. It starts with secure coding, which should be an integral part of the development process. Code analysis tools are available which include the insertion of random data into the inputs and running test case scenarios. Validating inputs is essential, where input is checked to ensure that it conforms to rigid specifications, including length, type of input, the full range of acceptable values, missing or extra inputs, syntax, consistency across related fields, and conformance to business rules. Employ “least privilege” with an understanding of what levels of access individual users really need. Also, Admin privileges should be provisioned so that there’s a barrier between the database application and other applications on the system or the operating system itself. Techniques such as stored procedures and parameterized queries can prevent the implementation of bad commands masked as variables.
Manufacturers and end-users both can use the services of outside organizations to perform penetration testing on their applications and networks. Representatives of both Lenel and Software House confirmed to me that they do this. End users should also make sure that their servers are cyber-hardened, consider Intrusion Detection and Intrusion Prevention systems, and subscribe to the Defense in Depth concept.
Knowledge is Power
Integrators and end-users alike should ask the hard questions of the manufacturers about means taken to cyber-harden applications. But it’s more vital that security professionals should make it their business to become as knowledgeable as possible! These threats are increasingly complex and attack tools are only becoming easier to use.